Operations Task Management for Azure Alerts
A few weeks back, a customer asked us for a way to effectively track the alerts that they get from Microsoft Sentinel and Defender for Cloud and ensure resolution. For organisations with an ITIL practice, this work is tracked by logging an Incident or a Problem ticket in an ITSM tool. But some organisations are a lot leaner (no ITIL practice and no ITSM tooling) and simply need something that works.
This article is also posted in the Azure Architecture Blog.
Solution Idea
And so the idea is to use Azure Boards as a simple Kanban board for the operations team to track work status. The tasks are created automatically as alerts/incidents are raised using Azure Logic Apps.
Workflow
But before that, let’s design the workflow:
graph LR
A[Defender Alert] -- create --> B[Work Item Type = Problem]
B --> F
C[Sentinel Incident] -- create --> E[Work Item Type = Issue]
D[Sentinel Alert] -- create --> E
E --> F[State = New]
F --> G[State = Approved]
F --> H[State = Removed]
G --> I[State = Active]
I --> J[State = Verification]
J -- Update Reference Incident/Alert --> K[State = Closed]
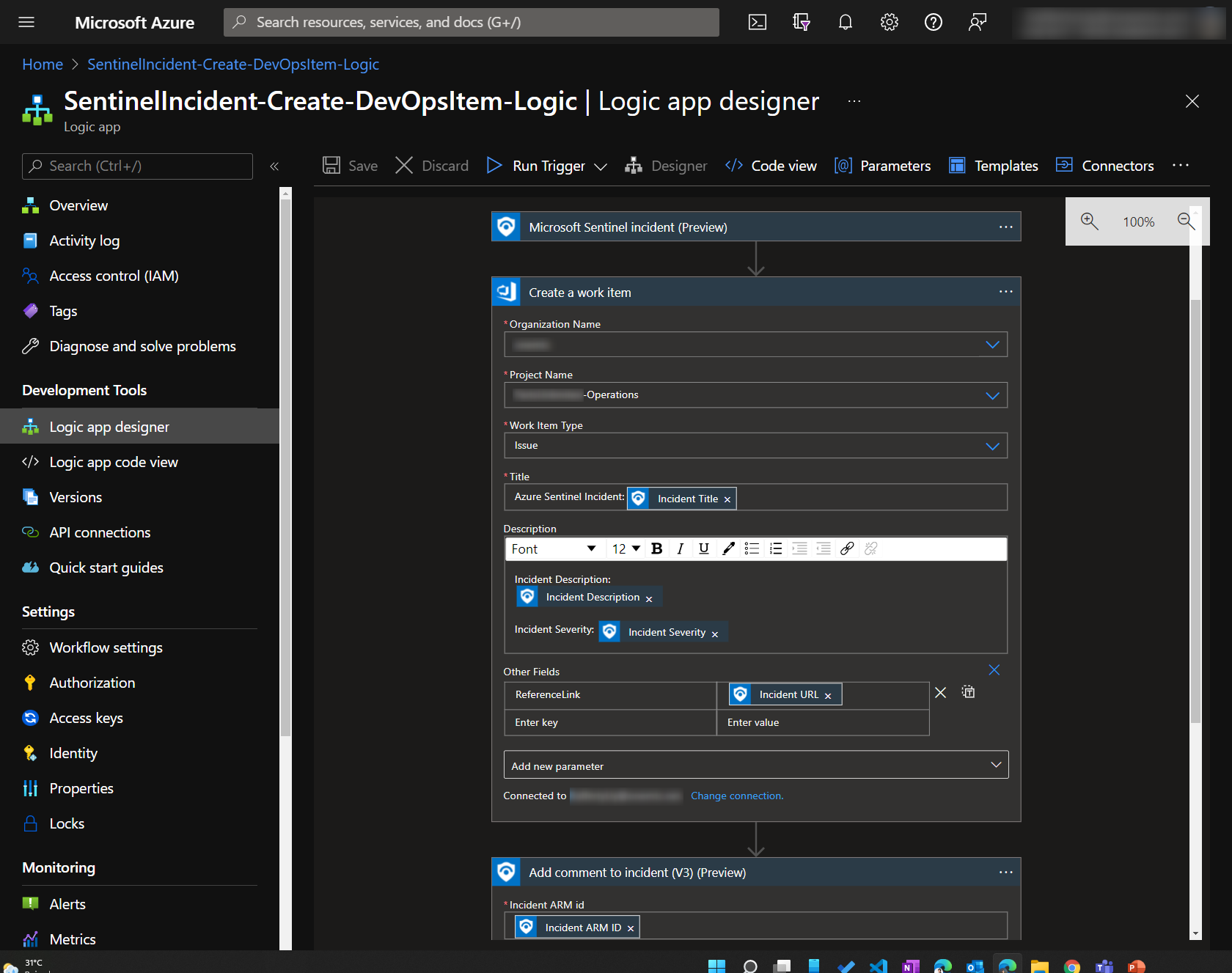
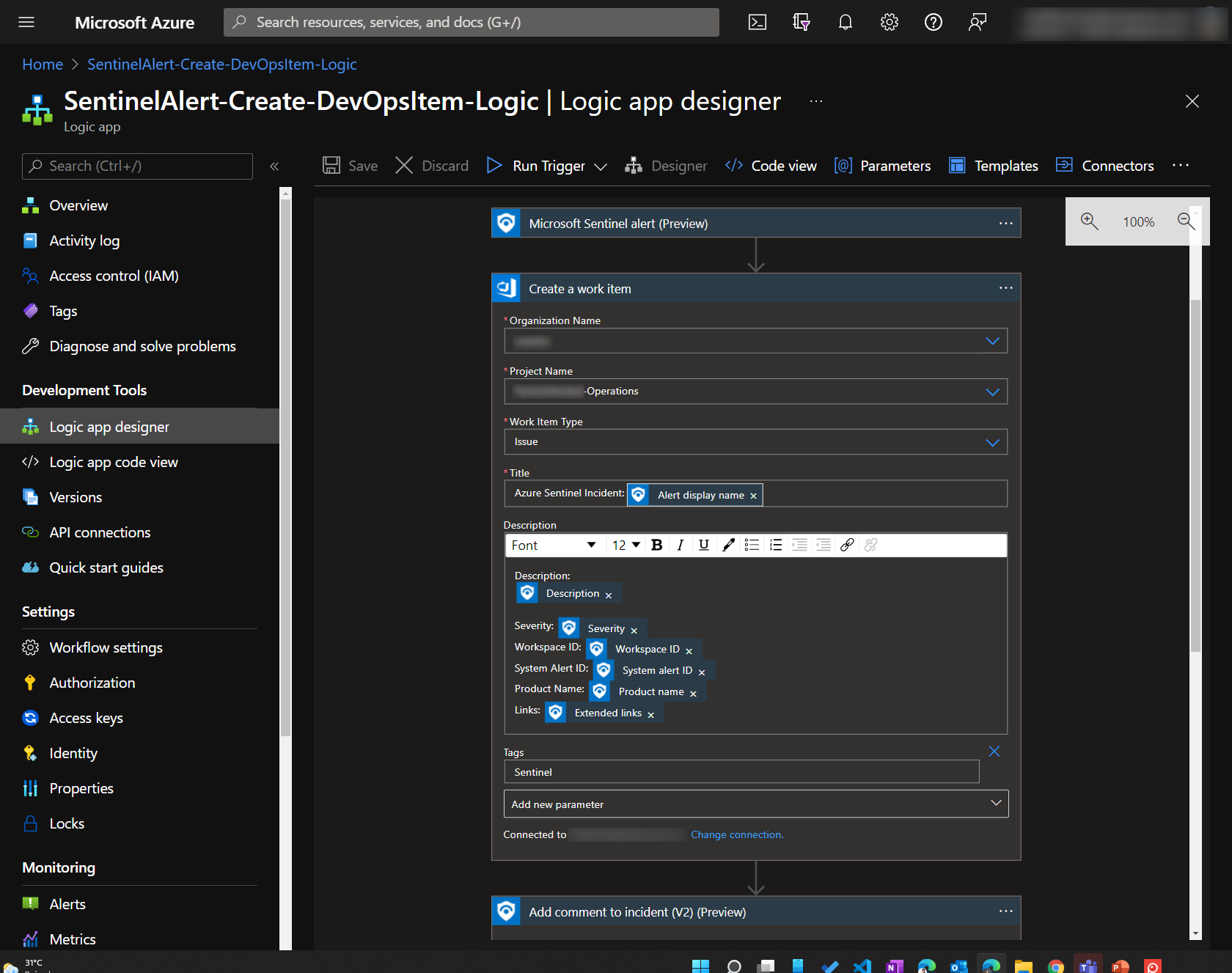
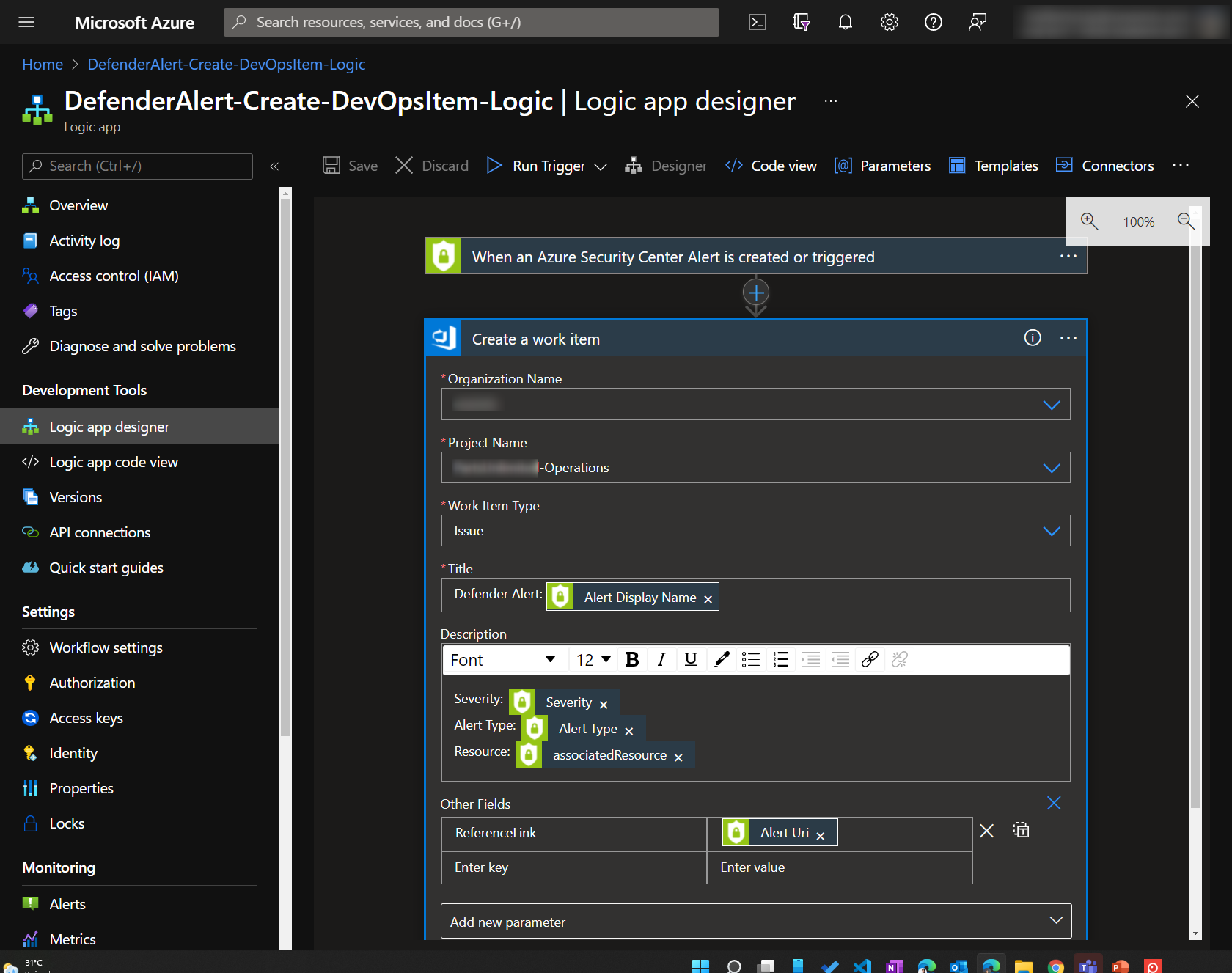
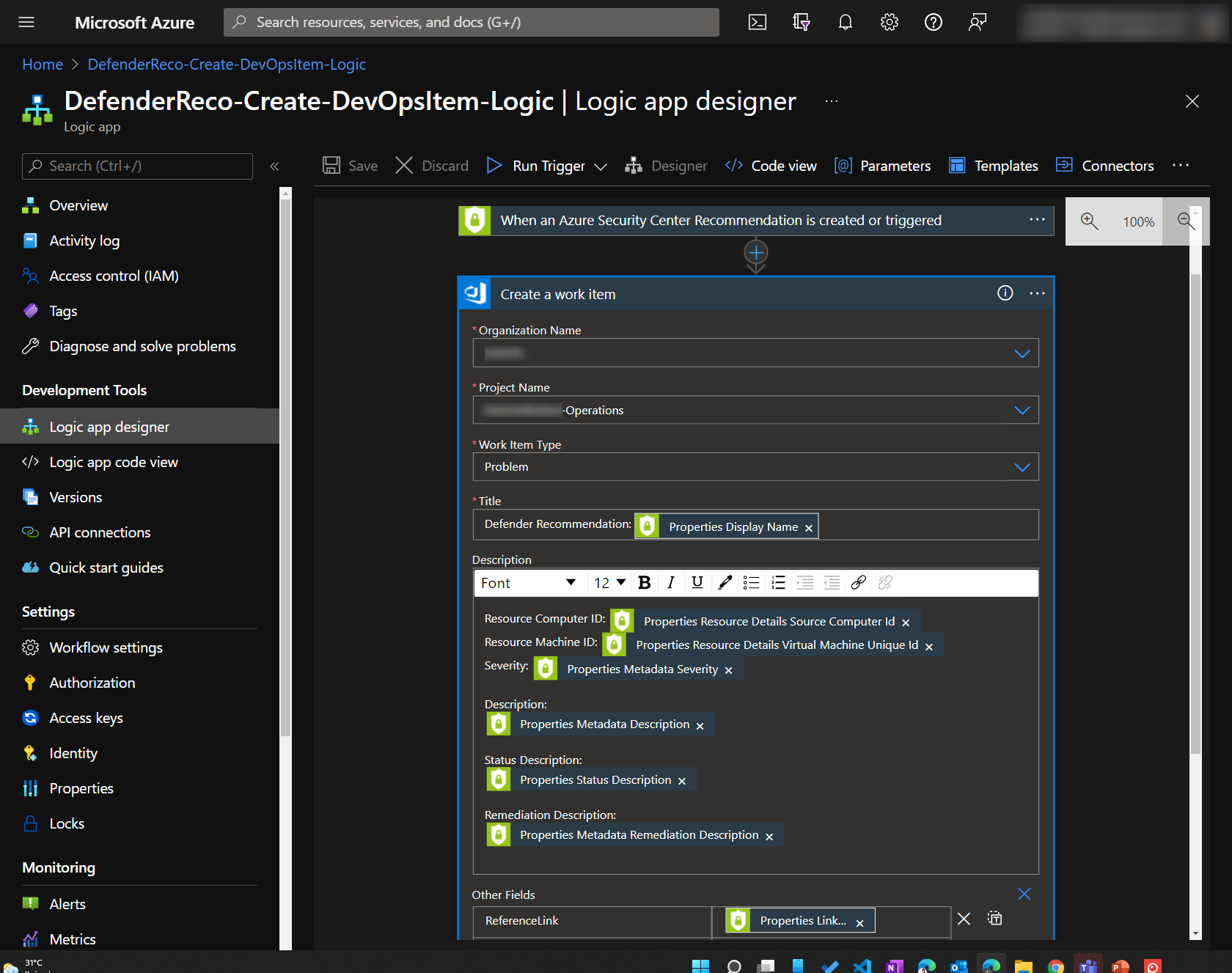
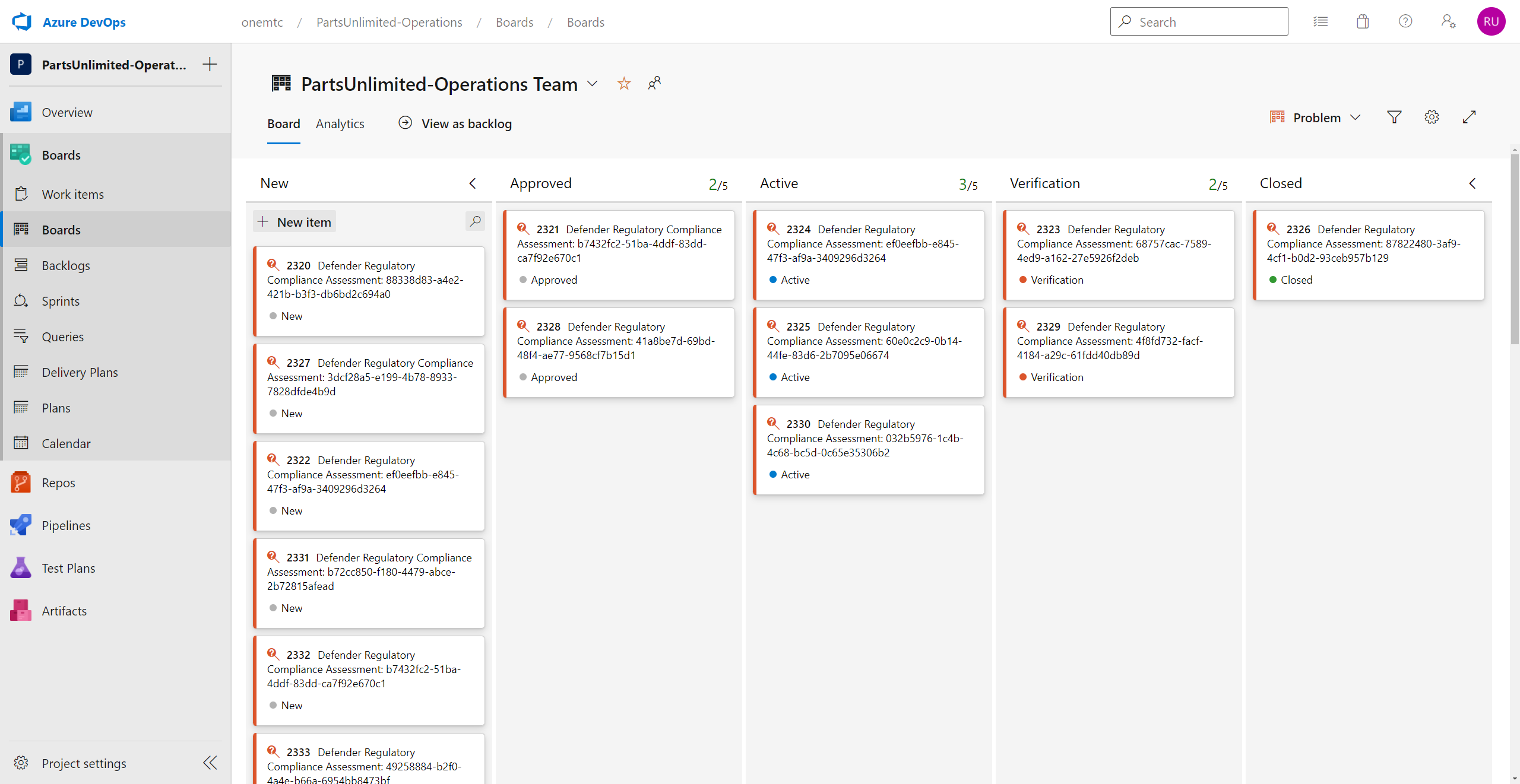
This workflow is implemented using a custom inherited process in Azure Boards. In our implementation, we used Work Item Type=Issue for Incident-type items, typically coming from Microsoft Sentinel, and Work Item Type=Problem for Problem-type items, typically coming from Defender for Cloud recommendations Since items are created automatically in Azure Boards, there is a need to clean up the alerts and reduce false positives. The work items are also first triaged and approved/removed before work is done. An extra verification stage is added for review before resolution.
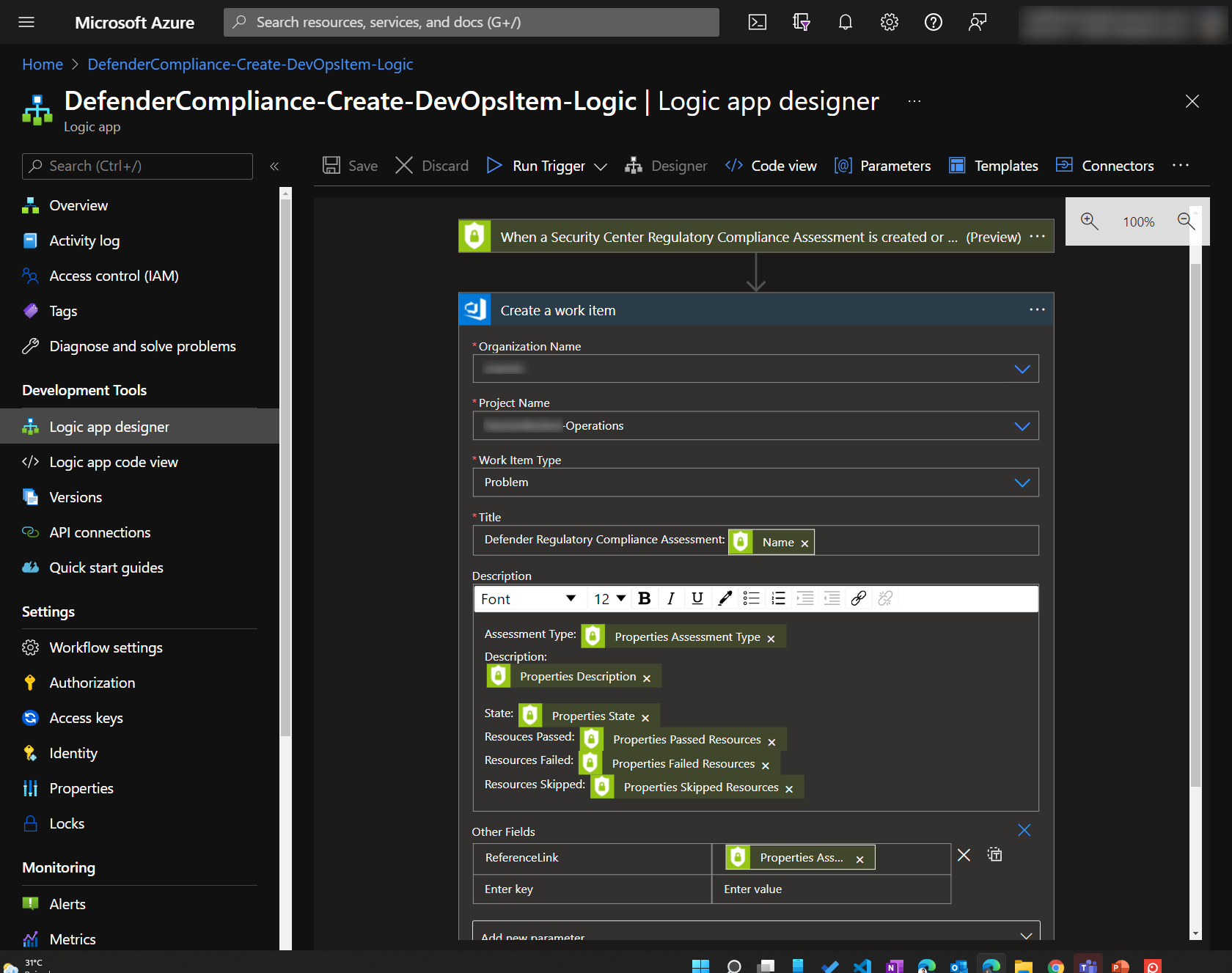
The Logic Apps
Creating the logic apps was easy. Microsoft already provided templates to deploy these logic apps in our Azure Subscription.
- Create DevOps Tasks from Microsoft Defender. Then duplicate this task and create separate triggers for Defender Alerts, Recommendations and Regulatory Compliance.
- Create DevOps Tasks from Microsoft Sentinel
Here are some screenshots
Result
Future Work
At the moment, we expect the work item owner to update/resolve the alert in Microsoft Defender/Sentinel manually as they complete the work. This can be optimised further by creating a webhook upon work item update, which in turn calls a logic app that resolves the linked Sentinel or Defender alert.
flowchart LR
A[Work Item Updated] -- webhook --> B[Logic App]
B --> C{Is State=Closed?}
C -- Yes --> D[Update Incident/Alert]
C -- No --> E[Do nothing]
The Logic App can be implemented using the following connector actions:
Update: This is implemented, see here To see the code, check out my GitHub repo.